Cryptocurrency Prices by Coinlib

Stealing Crypto Credentials from Your Screen – ELLIPAL
Introduction
In an ever-evolving digital landscape, cybersecurity threats are becoming more sophisticated. Recently, a concerning trend has emerged where Android apps utilize Optical Character Recognition (OCR) to illicitly capture cryptocurrency credentials. This blog explores how these threats operate and how ELLIPAL's secure technology offers a robust defense.
What is OCR?
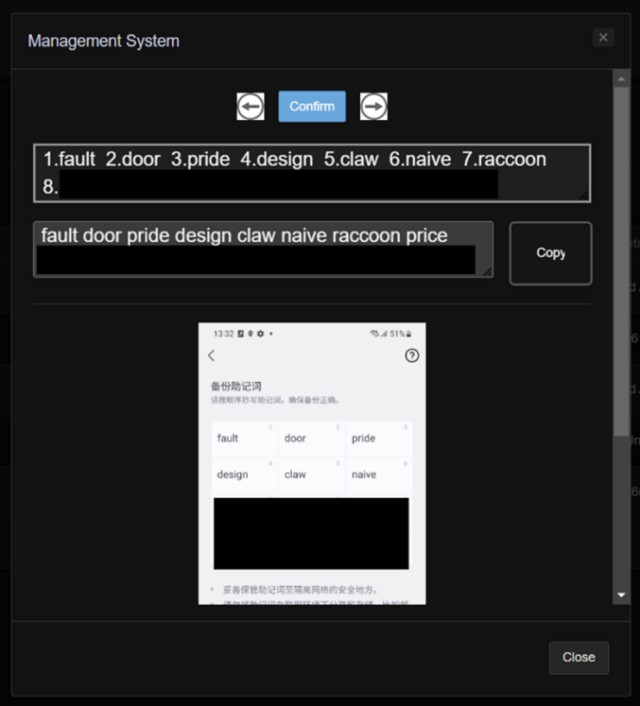
Optical Character Recognition (OCR) technology transforms images of text into editable and searchable data. Unfortunately, this innovative tool is now being exploited by malicious apps to steal sensitive information directly from users' screens.
The Threat Unveiled
According to a detailed report by Ars Technica, about 280 Android apps have been identified as using OCR to secretly steal cryptocurrency information. These apps, often disguised as legitimate utilities, slyly capture wallet credentials and seed phrases when users access their digital wallets.
Impact on Cryptocurrency Users
The implications of such attacks are severe. Users could face substantial financial losses and irreparable damage to their privacy. The primary target of these attacks-cryptocurrency credentials-are crucial for accessing and managing digital assets securely.
How ELLIPAL Protects You
Unlike traditional mobile and web wallets, ELLIPAL operates on a principle of complete offline security. Our cold wallets are designed to store your cryptocurrency credentials 100% offline, making it impossible for OCR-based malware to access your sensitive information.
- Physical Security: ELLIPAL's hardware wallets require physical verification for any transaction, keeping your data secure even if your computer or smartphone is compromised.
- No Internet Access: With no internet connectivity, there are no entry points for hackers to exploit using OCR or any other online-based attack vectors.
Steps to Enhance Your Security
- Be Vigilant: Always download apps from trusted sources and keep an eye out for any unusual permissions requested during installation.
- Regular Updates: Keep your devices and apps updated to protect against known vulnerabilities.
- Secure Backup: Store backup phrases and private keys in physically secure locations away from internet access.
